Get Dell ESX host warranty info via PowerCLI version 3
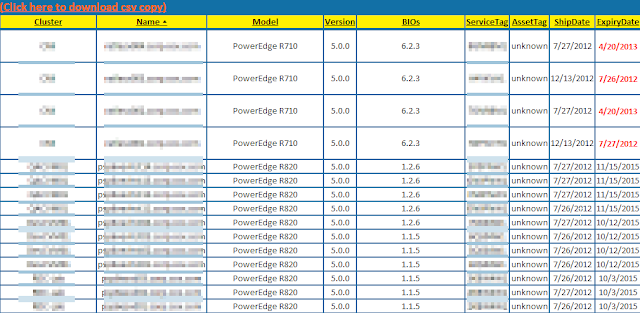
Summary: Had a script that was doing a screen scrape of Dell's support page for warranty info. Now they require a log in. So it was time to finally revise my script to use Dell's wsdl (SOAP) interface. Example: Details: I was able to simplify the script a bit using the code provided by Jon Gurgul to pull from Dell's provided SOAP service. I copied the code into a Get-DellAssetInformation.psm1 file so I could call the function as a module. The variable you should probably update is the $ServiceDescription variable to match the warranty type you expect from your boxes so you get an actual return of data. I simply plugged this into my existing code removing the screen scrape code and this is what I ended up with: Script: Add-PSsnapin VMware.VimAutomation.Core #Module code courtesy of Jon Gurgul Import-Module C:\myModuleDirectory\Get-DellAssetInformation.psm1 $VIServer = Connect-VIServer myvCenterServer $date = Get-Date $htmpath ...

