vCenter Permissions/Roles overkill? maybe? maybe not… specifically with View 4.0.1
Related Products:
When creating a View Desktop Pool, no folder path, or datastores are presented and a whole other slew of errors should you decide NOT to grant the administrator role to the View Composer Service Account.
Resolution:
View Composer Role permissions need to be granted in 1 or 6 places in vCenter depending on how restricted the account should be. 1 place would be to grant the administrator role to the View Composer Service Account @ the vCenter Node Level and propagate down. If the aim to to restrict access to one cluster/host, then the View Composer Role must be applied to the following areas:
Pictures are provided as an example and are not a reflection of how all vCenter servers are configured/designed.
I came across something interesting today while I was setting up my production View environment. One of the requirements when setting up View Composer is that it needs an account that has be part of the administrator group of the Windows OS on the vCenter server. Not a big deal since we don’t grant access to “BuiltIn\Administrators” rights to vCenter itself.
Now granted, the service account needs rights to vCenter which is up next, requirements state that the vCenter Composer service account be granted what VMWare calls the “View Composer” Role. ACTUAL View Composer Role Permissions needed, to break it down on one table here it is:
[UPDATED Permissions Table found HERE]
- VMWare View 4.0.1
- VMWare vCenter 4.0 U1
When creating a View Desktop Pool, no folder path, or datastores are presented and a whole other slew of errors should you decide NOT to grant the administrator role to the View Composer Service Account.
Resolution:
View Composer Role permissions need to be granted in 1 or 6 places in vCenter depending on how restricted the account should be. 1 place would be to grant the administrator role to the View Composer Service Account @ the vCenter Node Level and propagate down. If the aim to to restrict access to one cluster/host, then the View Composer Role must be applied to the following areas:
Pictures are provided as an example and are not a reflection of how all vCenter servers are configured/designed.
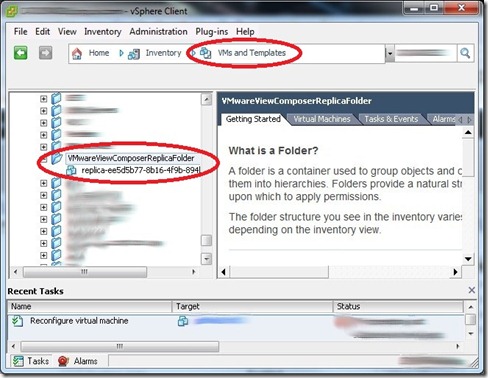
- VM and Templates – Role added to Chosen Target Folder, Gold Image Folder, and the “VMWareViewComposerReplicaFolder”
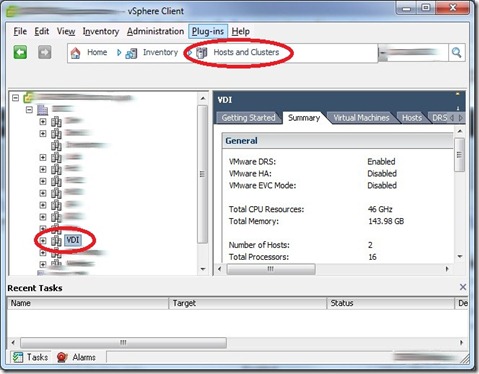
- Hosts and Clusters – Role added to Host | Cluster
- Datastores – Role added to Datastores related to Cluster or Host chosen.
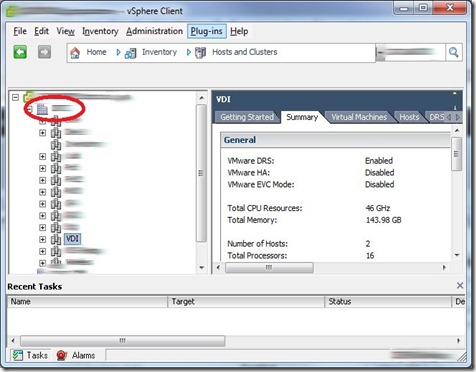
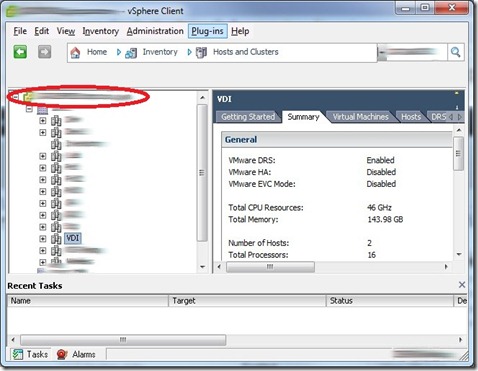
- Datacenter – Role added to Datacenter node, do NOT propagate the View Composer Role permission.
- vCenter – This would be the name of your vCenter server, Add the role to this node, do NOT propagate.
- Networking – All networks would need to be sorted into folders and your service account granted read-only permissions all networks or just ones you specify.
I came across something interesting today while I was setting up my production View environment. One of the requirements when setting up View Composer is that it needs an account that has be part of the administrator group of the Windows OS on the vCenter server. Not a big deal since we don’t grant access to “BuiltIn\Administrators” rights to vCenter itself.
Now granted, the service account needs rights to vCenter which is up next, requirements state that the vCenter Composer service account be granted what VMWare calls the “View Composer” Role. ACTUAL View Composer Role Permissions needed, to break it down on one table here it is:
[UPDATED Permissions Table found HERE]
| Privilege Group | Privilege(s) to Enable |
| Folder | Create Folder Delete Folder |
| Datastore | Browse Datastore File Management - (This is listed in the admin guide, VMWare needs to clarify this.) My understanding is the following: Allocate Space Remove File |
| Virtual Machine | Inventory (All Rights) Configuration (All Rights) Interaction > Power On Interaction > Power Off Interaction > Suspend Interaction > Reset State Provisioning > Clone Provisioning > Allow Disk Access Provisioning > Deploy Template Provisioning > Read Customization Specifications |
| Resource | Assign Virtual Machine to Resource Pool |
| Global | Enable Methods Disable Methods NOT in the admin guide: System Tag Global Tag |
| Network | NOT in the admin guide: Assign Network |
| Sessions | NOT in the admin guide: Validate session View and Stop sessions |




Comments
To me, it is another example why I recommend a separate vCenter for Desktop.
e1 @ vmware.com