Mac: VPN over SSH using sshuttle
Summary:
Sometimes it's simply easier to run or do things from your local system rather than rely on a bastion/jumphost. sshuttle allows you to utilize a Linux bastion/jumphost as a psuedo VPN endpoint.
Full documentation and source can be found here:
http://sshuttle.readthedocs.io/en/stable/manpage.html
https://github.com/apenwarr/sshuttle
Walkthrough:
Brew is probably the easiest installation method and less prone to complications by using pip. So that's what I'll go through here:
- Launch Terminal
- brew install sshuttle
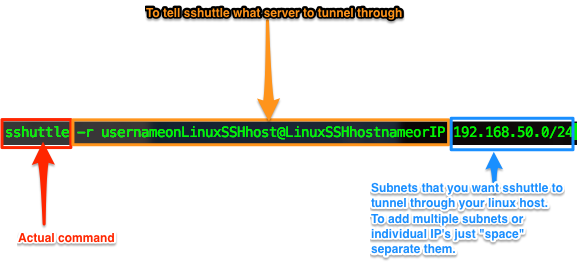
- sshuttle -r usernameonLinuxSSHhost@LinuxSSHhostnameorIP 192.168.50.0/24
Done. Easy right? Now upon successful connection, all traffic bound for an ip on 192.168.50.0/24 will tunnel through your Linux SSH host.
Additional Notes:
Remember to kill your session when done. I've heard of reports that sshuttle having memory leaks or whatnot causing RAM to fill up. Killing terminal session should kill it, but you may need to kill in activity monitor.
This type of tunneling can also be done on Windows via SOCKS5 proxying. You can find details on how to do that here:
https://www.digitalocean.com/community/tutorials/how-to-route-web-traffic-securely-without-a-vpn-using-a-socks-tunnel
Handy Firefox add-on for selective proxying:
https://addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard/
This type of tunneling can also be done on Windows via SOCKS5 proxying. You can find details on how to do that here:
https://www.digitalocean.com/community/tutorials/how-to-route-web-traffic-securely-without-a-vpn-using-a-socks-tunnel
Handy Firefox add-on for selective proxying:
https://addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard/



Comments